Product
Pricing
Partners

On July 1, 2021, The U.S. National Security Agency (NSA), Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), and the UK’s National Cyber Security Centre (NCSC) released a joint advisory around the ongoing, high-impact targeted attacks on organizations using Microsoft Office 365 cloud services.
Although all Microsoft Office 365 organizations are at risk, there is a heightened risk for those in hybrid environments within government, defense, energy, and higher education branches.
The advisory released on July 1st indicates a higher use of brute force attacks on email and user accounts for those operating in the Microsoft Office 365 space. Lateral movement into administrative accounts; remote code execution; malware; ransomware; creation of back-door access for future use.

When looking at extensive analysis in the attempt to gather insightful infrastructure data – it pays to invest in reliable log management tools that can empower your business workflow.
Utilizing an automated log management tool is beneficial in three key areas.
Through the CoreView Health Check, you can enable logging and surface operational issues based on your specific tenant.
Indicators of compromise act as a warning system to alert the IT pro to hazardous activity early. These unusual activities are the red flags that indicate a potential or in-progress attack that could lead to a data breach or systems compromise.
These red flags should not be taken lightly and should insight action internally to help mitigate risk and protect your data. CoreView was founded on providing quick action reports to these potential threats and provides a set of reporting that stays one step ahead. Reports like ‘Email Forwarding Outside the Domain’ and ‘Exchange New Management Role Assignment’ are already in place to ensure malicious activity remains at bay.
Set blocks as described in Block access [via Conditional Access Policy] from anonymous IP addresses, below.
Although PowerShell is generally treated as a trusted application by security software– it has also become an increasingly popular avenue for malware attacks.
By utilizing CoreView Custom Actions for M365 PowerShell Commands, these accounts are secured with a CoreView service account leveraging Azure Key Vault services and customers’ own Conditional Access policies – invulnerable to these exploits. End users do not need access to remote PowerShell, thus meeting the recommendations.
Human error is one of the top reasons for data breaches in the cloud, as administrators forget to turn on basic security controls. By reducing the number of hands in the kitchen you will be able to provide greater control of your ecosystem and ensure it runs smoothly.
Azure AD does not provide controls for Session time-out and lockout policies. Surprisingly, without session controls such as CoreView’s “Revoke User Sessions” management action, the session timeouts are up to 90 days for SharePoint Online mobile access, 5 days for SPO client access, 8 hours for the M365 admin center, and 6 hours for OWA.
For Yammer access it is forever, and for Azure AD, “Refresh tokens are valid for 90 days, and with continuous use, they can be valid until revoked.”
If you detect that someone has launched a brute-force attack against your site (such attacks generate a huge amount of fail login attempts in your log), you can block the attacker’s IP address from accessing your site completely.
CoreView can easily pinpoint the location where that anonymous traffic has come from and provide an easy solution to shut down the attacks.
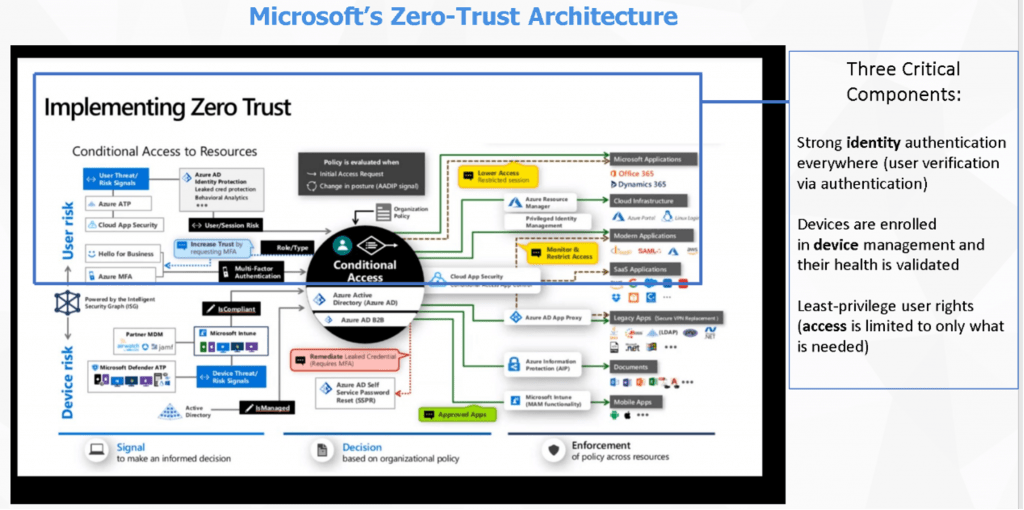
According to Microsoft, their own Zero-Trust implementation… “journey began a few years ago and will continue to evolve for years to come”
CoreView’s management actions and reports provide configuration and constant validation of critical Microsoft Zero Trust elements, specifically for Identity Management, Device Management, and Least-Privilege Access.
CoreView speeds the time-to-value of the critical components highlighted below to weeks. Here are some resources: